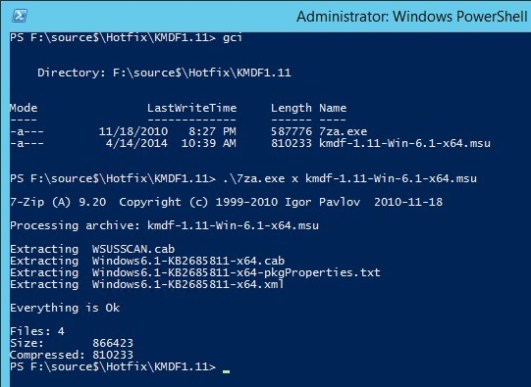
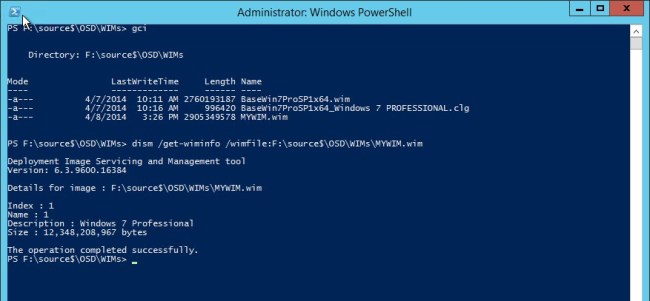
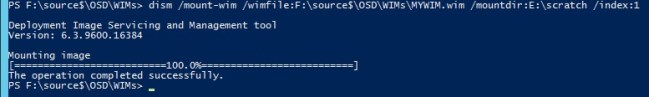
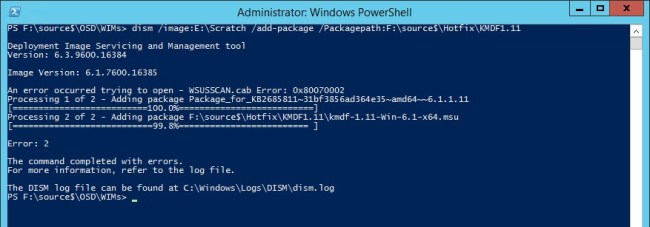
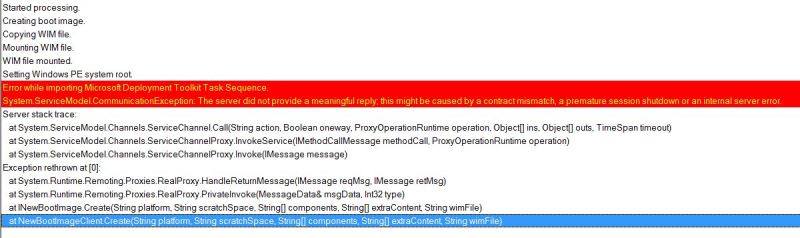
I’ve created a toll for downloading the bits for Update Rollup 2, as well as extracting the .cab files. This keeps it a bit more organized and is quicker than navigating through windows update. Enjoy!
<#
.SYNOPSIS
Downloads all of UR2 (english only)
.DESCRIPTION
All prereqs are downloaded and unpacked
.INPUTS
-DestinationFoler
used to define the location where everything is stored. Default is C:\SysCen2012R2UR2
-Cleanup
true/false used to delete cab files after expanding. Default is $true
.OUTPUTS
None
.NOTES
Author: Daniel Kucinski
Date: June 2014
Purpose/Change: Initial creation
.EXAMPLE
.\SCUR2downloader.ps1 -DestinationFolder c:\UpdateRollup2 -CleanUp $true -Verbose
.EXAMPLE
...just right-click and run enjoy!
#>
[CmdletBinding(SupportsShouldProcess=$true, ConfirmImpact='High')]
param(
[Parameter(position=0)]
[string]$DestinationFolder = "C:\SysCen2012R2UR2",
[Parameter(position=1)] #Mandatory=$true
[bool]$CleanUp = $true
)
$erroractionpreference = "SilentlyContinue"
$error.clear()
$download = New-Object System.Net.WebClient
function Expand-ZIPFile($file, $destination) {
$shell = New-Object -ComObject shell.application
$zip = $shell.NameSpace($file)
ForEach ($item in $zip.items())
{
$shell.NameSpace($destination).CopyHere($item,0x14)
} #foreach
} #function
# create dir and download prereqs from MS
[array]$components = @("VMM","SCSM","SCO","SCOM","SPF","SMA","DPM")
New-Item -Type directory -path $DestinationFolder | Out-Null
ForEach ($item in $components) {
New-Item -Type directory -Path $DestinationFolder\$item | Out-Null
} #foreach
Write-Verbose "created directories - continuing..."
# SCSM
IF (Test-Path "$DestinationFolder\SCSM\SCSM2012R2_CU_KB2904710_AMD64_7.5.3079.61.exe") {
Write-Verbose "SCSM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCSM components"
$source = "http://download.microsoft.com/download/1/6/A/16A55195-AA6A-4210-A780-0403D7F7D6EE/SCSM2012R2_CU_KB2904710_AMD64_7.5.3079.61.exe"
$destination = "$DestinationFolder\SCSM\SCSM2012R2_CU_KB2904710_AMD64_7.5.3079.61.exe"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# SCOM
#management server
IF (Test-Path "$DestinationFolder\SCOM\kb2929891-amd64-server_efa0a2029f892ab08b3b5c869fe57f8c267dc6e6.cab") {
Write-Verbose "SCSM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCOM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2929891-amd64-server_efa0a2029f892ab08b3b5c869fe57f8c267dc6e6.cab"
$destination = "$DestinationFolder\SCOM\kb2929891-amd64-server_efa0a2029f892ab08b3b5c869fe57f8c267dc6e6.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#gateway
IF (Test-Path "$DestinationFolder\SCOM\kb2929891-amd64-gateway_6c78f8fcacf5e679d6ef63398fb6538322c92e98.cab") {
Write-Verbose "SCSM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCOM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2929891-amd64-gateway_6c78f8fcacf5e679d6ef63398fb6538322c92e98.cab"
$destination = "$DestinationFolder\SCOM\kb2929891-amd64-gateway_6c78f8fcacf5e679d6ef63398fb6538322c92e98.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#webconsole
IF (Test-Path "$DestinationFolder\SCOM\kb2929891-amd64-enu-webconsole_f459a18aa85e98d6270fe6bbbeb26ed29ebab466.cab") {
Write-Verbose "SCSM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCOM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2929891-amd64-enu-webconsole_f459a18aa85e98d6270fe6bbbeb26ed29ebab466.cab"
$destination = "$DestinationFolder\SCOM\kb2929891-amd64-enu-webconsole_f459a18aa85e98d6270fe6bbbeb26ed29ebab466.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# SMA
IF (Test-Path "$DestinationFolder\SMA\kb2904689_powershellmoduleinstaller_x64_d57fd83f3066ad603201e3d42630cbd00bc28e67.cab") {
Write-Verbose "SCSM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCOM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2904689_powershellmoduleinstaller_x64_d57fd83f3066ad603201e3d42630cbd00bc28e67.cab"
$destination = "$DestinationFolder\SMA\kb2904689_powershellmoduleinstaller_x64_d57fd83f3066ad603201e3d42630cbd00bc28e67.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# SPF
IF (Test-Path "$DestinationFolder\SPF\kb2932939_microsoft.systemcenter.foundation.setup_x64_0a38ef61d7850cfb903492670e3fa3cf6c8471f3.cab") {
Write-Verbose "SPF Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCOM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2932939_microsoft.systemcenter.foundation.setup_x64_0a38ef61d7850cfb903492670e3fa3cf6c8471f3.cab"
$destination = "$DestinationFolder\SPF\kb2932939_microsoft.systemcenter.foundation.setup_x64_0a38ef61d7850cfb903492670e3fa3cf6c8471f3.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# VMM
#adminconsole x64
IF (Test-Path "$DestinationFolder\VMM\kb2932942_adminconsole_amd64_5dd291de44899042205ec70eecb8555f1c2c10d0.cab") {
Write-Verbose "VMM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading VMM components"
$source = "http://download.windowsupdate.com/c/msdownload/update/software/uprl/2014/04/kb2932942_adminconsole_amd64_5dd291de44899042205ec70eecb8555f1c2c10d0.cab"
$destination = "$DestinationFolder\VMM\kb2932942_adminconsole_amd64_5dd291de44899042205ec70eecb8555f1c2c10d0.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#VMM server
IF (Test-Path "$DestinationFolder\VMM\kb2932926_vmmserver_amd64_ebd2c3f90127efa11f750f1464cb44bd1b0108bc.cab") {
Write-Verbose "VMM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading VMM components"
$source = "http://download.windowsupdate.com/c/msdownload/update/software/uprl/2014/04/kb2932926_vmmserver_amd64_ebd2c3f90127efa11f750f1464cb44bd1b0108bc.cab"
$destination = "$DestinationFolder\VMM\kb2932926_vmmserver_amd64_ebd2c3f90127efa11f750f1464cb44bd1b0108bc.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# SCO
#webservice
IF (Test-Path "$DestinationFolder\SCO\kb2904689_webserviceinstaller_x64_fa0016be99b73e5738d9a30068ca93566d26a622.cab") {
Write-Verbose "VMM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading VMM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2904689_webserviceinstaller_x64_fa0016be99b73e5738d9a30068ca93566d26a622.cab"
$destination = "$DestinationFolder\SCO\kb2904689_webserviceinstaller_x64_fa0016be99b73e5738d9a30068ca93566d26a622.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#runbook server
IF (Test-Path "$DestinationFolder\SCO\kb2904689_runbookserver_x86_4cfc6f108fc6432d251ab861401ceeb6c93acd8a.cab") {
Write-Verbose "SCO Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCO components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2904689_runbookserver_x86_4cfc6f108fc6432d251ab861401ceeb6c93acd8a.cab"
$destination = "$DestinationFolder\SCO\kb2904689_runbookserver_x86_4cfc6f108fc6432d251ab861401ceeb6c93acd8a.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#runbook designer
IF (Test-Path "$DestinationFolder\SCO\kb2904689_runbookdesigner_x86_55fa0a511b6def5b80e72f7edb162277b32b9ae9.cab") {
Write-Verbose "SCO Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading SCO components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/04/kb2904689_runbookdesigner_x86_55fa0a511b6def5b80e72f7edb162277b32b9ae9.cab"
$destination = "$DestinationFolder\SCO\kb2904689_runbookdesigner_x86_55fa0a511b6def5b80e72f7edb162277b32b9ae9.cab"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# DPM
#central console server
IF (Test-Path "$DestinationFolder\DPM\dpmcentralconsoleserver-kb2963543_ce185cdaad05fb7f5df55a6b14883eede2c031b2.exe") {
Write-Verbose "DPM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading DPM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/05/dpmcentralconsoleserver-kb2963543_ce185cdaad05fb7f5df55a6b14883eede2c031b2.exe"
$destination = "$DestinationFolder\DPM\dpmcentralconsoleserver-kb2963543_ce185cdaad05fb7f5df55a6b14883eede2c031b2.exe"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#dpm
IF (Test-Path "$DestinationFolder\DPM\dataprotectionmanager2012r2-kb2963543_a975a99c79b2c1267f3087dc34af68398994849d.exe") {
Write-Verbose "DPM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading DPM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/05/dataprotectionmanager2012r2-kb2963543_a975a99c79b2c1267f3087dc34af68398994849d.exe"
$destination = "$DestinationFolder\DPM\dataprotectionmanager2012r2-kb2963543_a975a99c79b2c1267f3087dc34af68398994849d.exe"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#management shell 1
IF (Test-Path "$DestinationFolder\DPM\dpmmanagementshell-kb2963543_015ac9652a3cbb3fef17496fdaf90a0b64feeb95.exe") {
Write-Verbose "DPM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading DPM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/05/dpmmanagementshell-kb2963543_015ac9652a3cbb3fef17496fdaf90a0b64feeb95.exe"
$destination = "$DestinationFolder\DPM\dpmmanagementshell-kb2963543_015ac9652a3cbb3fef17496fdaf90a0b64feeb95.exe"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
#management shell 2
IF (Test-Path "$DestinationFolder\DPM\dpmmanagementshell-kb2963543_7e533fb1e095022cb8a4298af77c139ae0c34bd7.exe") {
Write-Verbose "DPM Update Rollup 2 located"
}
ELSE {
Write-Verbose "Downloading DPM components"
$source = "http://download.windowsupdate.com/d/msdownload/update/software/uprl/2014/05/dpmmanagementshell-kb2963543_7e533fb1e095022cb8a4298af77c139ae0c34bd7.exe"
$destination = "$DestinationFolder\DPM\dpmmanagementshell-kb2963543_7e533fb1e095022cb8a4298af77c139ae0c34bd7.exe"
Invoke-WebRequest -Uri $source -OutFile $destination
Write-Verbose "Downloaded $destination"
} #else
# unzip cab files
$Cabs = Get-ChildItem -Path $DestinationFolder -Recurse -Filter *.cab
foreach ($cab in $cabs) {
#$FriendlyName =
Write-Verbose "Expanding $Cab.BaseName"
Expand-ZIPFile –File $Cab.FullName –Destination $Cab.DirectoryName
Write-Verbose "done..."
} #foreach
# cleanup
IF ($CleanUp -eq $true) {
foreach ($cab in $cabs) {
#$FriendlyName =
Write-Verbose "Deleting $Cab.BaseName"
Remove-Item $Cab.FullName -Force
Write-Verbose "done..."
} #foreach
} #IF